 Several acquaintances of mine have been stung in recent months by the rogue program “Antispyware XP2009″. This program relies on social engineering to dupe you into installing a malicious program to then extort money.
Several acquaintances of mine have been stung in recent months by the rogue program “Antispyware XP2009″. This program relies on social engineering to dupe you into installing a malicious program to then extort money.
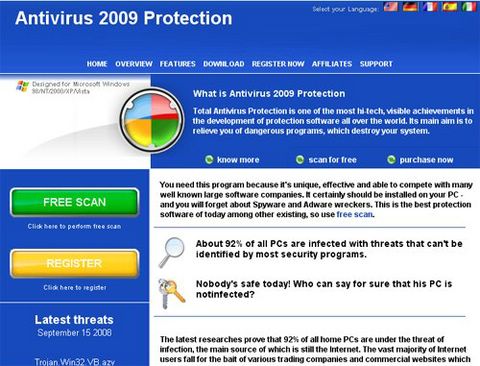
Looks legitimate right? Here’s how it works. You visit a website, and without warning, an ominous message appears on screen alerting you that spyware or a virus has been detected on your machine with the instructions to “click now to clean”. Unwittingly falling victim to this ploy can be costly in more ways than one.
When you “click to clean”, this trojan installs Antispyware XP2009 on your system “for free”. After you perform their “free” scan, the software instructs you that you must purchase a license to remove the infected items it “finds”. Unfortunately the one infected or malicious item it never finds is itself. Paying the ransom, er, “license fee” does nothing except extort money from you. In addition, Antispyware XP2009 destroys legitimate program executable files, rendering popular programs such as Windows Media Player, Internet Explorer, Office applications and more, useless.
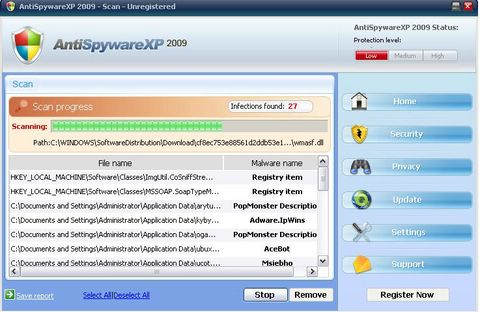
There are several copycat variants of this malware with similar names so surf cautiously! Your best defense against this type of attack is your own common sense. Never “click here” to clean anything that is presented unsolicited on any website. Also make sure you have a robust security solution that detects rogue applications and viruses in real time. Of course having robust anti-virus and anti-spyware are useless if threat definitions are not updated regularly, and that will be the subject of a future post! If you do fall victim to Antispyware XP 2009, contact the St. George PC Doctor to restore your computer’s health today.
![[KickIt]](http://www.dotnetkicks.com/favicon.ico)
![[Dzone]](http://www.dzone.com/favicon.ico)
![[Digg]](http://cdn1.diggstatic.com/img/favicon.a015f25c.ico)
![[Reddit]](http://www.reddit.com/favicon.ico)
![[del.icio.us]](http://www.delicious.com/favicon.ico)
![[Facebook]](http://www.facebook.com/favicon.ico)
![[Google]](http://www.google.com/favicon.ico)
![[StumbleUpon]](http://www.stumbleupon.com/favicon.ico)
![[Twitter]](http://stgeorgepcdoctor.com/pics/tweet.jpg)
Tags: spyware, virus, malware, threats, exploits, windows, critical updates, patches, antivirus